There are several generic restrictions on the content of shellcode. – There are several generic restrictions on the content of shellcode, which can significantly impact its development, deployment, and effectiveness. These restrictions are typically implemented to enhance security and prevent malicious activities. Understanding these limitations is crucial for both attackers and defenders in the realm of cybersecurity.
The following paragraphs delve into the specific types of restrictions commonly encountered, their impact on shellcode development, and techniques to overcome or mitigate these limitations. Additionally, the discussion explores the security implications and future trends in this area.
Common Restrictions on Shellcode Content
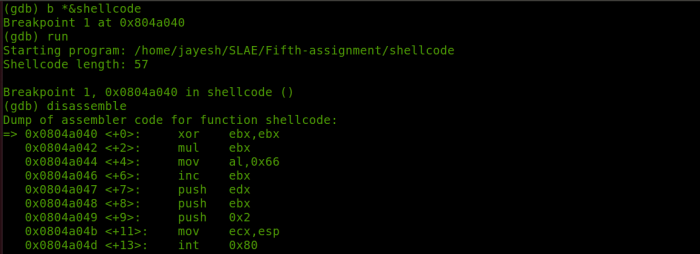
Restrictions on shellcode content are implemented to prevent malicious activities and maintain system integrity. These restrictions limit the types of instructions and data that can be included in shellcode, ensuring that it cannot perform unauthorized operations or compromise the system.
Types of Restrictions
- Size limitations:Shellcode is typically restricted to a specific size to prevent it from consuming excessive memory or causing buffer overflows.
- Instruction set restrictions:Some systems may restrict the use of certain instructions or opcodes within shellcode to prevent exploitation of vulnerabilities or system compromise.
- Data restrictions:Shellcode may be prohibited from accessing or modifying certain areas of memory, such as the kernel or sensitive user data, to prevent unauthorized access or data corruption.
- Function restrictions:Shellcode may be restricted from calling certain functions or APIs to prevent it from performing privileged operations or accessing sensitive resources.
Reasons for Restrictions
These restrictions are implemented to protect systems from malicious shellcode that could:
- Gain unauthorized access to sensitive data or system resources.
- Modify or corrupt system files or configurations.
- Install or execute malware or other malicious software.
- Exploit vulnerabilities to compromise the system’s integrity or security.
Impact of Restrictions on Shellcode Development
Content restrictions on shellcode pose challenges for developers who must work within these limitations to create effective and functional shellcode. These restrictions can:
- Limit the functionality of shellcode:Restrictions can prevent shellcode from performing certain tasks or accessing specific resources, which can limit its usefulness.
- Increase the complexity of shellcode development:Developers must find creative ways to bypass or work around restrictions while ensuring the shellcode remains functional.
- Increase the risk of detection:Shellcode that violates restrictions may be more easily detected by security mechanisms, increasing the risk of detection and analysis.
Techniques to Overcome Restrictions
Developers may use various techniques to overcome or mitigate the impact of restrictions, such as:
- Code obfuscation:Modifying the shellcode to make it less readable or detectable by security mechanisms.
- Polymorphism:Generating multiple versions of the shellcode with different signatures or patterns to evade detection.
- Encryption:Encrypting the shellcode to make it more difficult to analyze or reverse engineer.
Specific Examples of Restricted Content
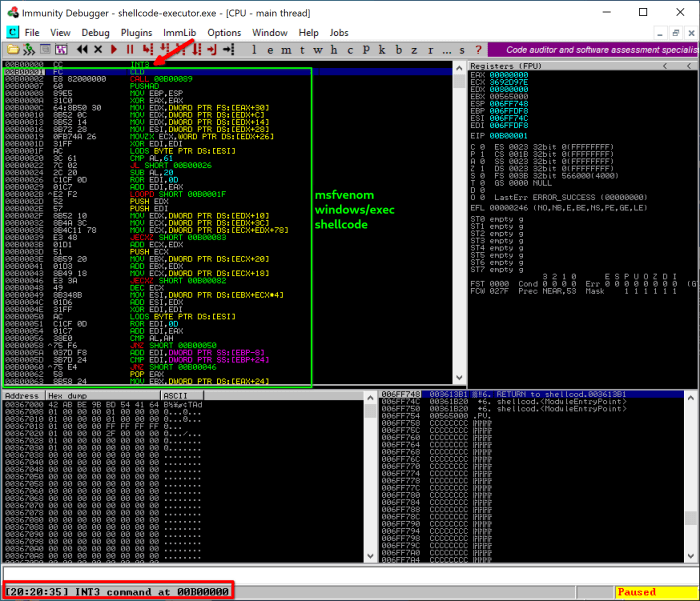
Specific types of content that are typically restricted in shellcode include:
- System calls:Shellcode may be prohibited from making certain system calls to prevent it from accessing sensitive resources or performing unauthorized operations.
- Memory access:Shellcode may be restricted from accessing or modifying certain areas of memory, such as the kernel or user data, to prevent unauthorized access or data corruption.
- Network access:Shellcode may be restricted from accessing the network or establishing connections to prevent it from communicating with external systems or exfiltrating data.
- Malicious instructions:Shellcode may be prohibited from executing certain instructions or opcodes that could be used to exploit vulnerabilities or compromise the system.
Consequences of Violating Restrictions
Violating content restrictions can have serious consequences, including:
- System compromise:Shellcode that violates restrictions could exploit vulnerabilities or compromise the system’s integrity or security.
- Detection and analysis:Shellcode that violates restrictions may be more easily detected by security mechanisms, leading to its analysis and potential neutralization.
- Legal penalties:In some cases, violating content restrictions may be considered a crime and could result in legal penalties.
Exceptions and Workarounds
There may be exceptions or loopholes in the enforcement of shellcode content restrictions. Attackers can potentially exploit these exceptions to bypass restrictions and execute malicious shellcode.
- Zero-day vulnerabilities:Attackers may discover and exploit zero-day vulnerabilities in security mechanisms to bypass restrictions.
- Exploiting legitimate functions:Attackers may find ways to exploit legitimate functions or APIs to perform restricted operations.
- Using alternative methods:Attackers may use alternative methods, such as code injection or process manipulation, to bypass restrictions and execute shellcode.
Techniques to Evade Detection and Analysis, There are several generic restrictions on the content of shellcode.
Attackers may use various techniques to evade detection and analysis of shellcode that violates restrictions, such as:
- Anti-debugging techniques:Shellcode can be modified to detect and evade debugging attempts.
- Virtualization:Shellcode can be executed within a virtual machine to isolate it from the host system and bypass restrictions.
- Code obfuscation:Shellcode can be obfuscated to make it more difficult to analyze or reverse engineer.
Security Implications
Content restrictions on shellcode have significant security implications.
Benefits of Restrictions
- Preventing malicious activities:Restrictions help prevent attackers from executing shellcode that could compromise the system’s integrity or security.
- Reducing the risk of data breaches:Restrictions can prevent shellcode from accessing or exfiltrating sensitive data.
- Improving system stability:Restrictions can prevent shellcode from causing system crashes or instability.
Drawbacks of Restrictions
- Limiting legitimate activities:Restrictions can also limit the use of shellcode for legitimate purposes, such as security research or system administration.
- Cat-and-mouse game:Attackers may find ways to bypass or exploit restrictions, leading to a continuous battle between attackers and defenders.
- False positives:Security mechanisms may sometimes誤報legitimate shellcode as malicious, leading to unnecessary system interruptions.
Future Trends and Developments
Future trends and developments in the area of shellcode content restrictions may include:
- Increased use of machine learning:Machine learning algorithms can be used to detect and analyze shellcode, potentially leading to more effective restrictions.
- Hardware-based restrictions:Hardware-based security features can be implemented to enforce content restrictions more effectively.
- New techniques to bypass restrictions:Attackers may develop new techniques to bypass or exploit restrictions, leading to an ongoing arms race between attackers and defenders.
FAQ Corner: There Are Several Generic Restrictions On The Content Of Shellcode.
What are the common types of restrictions on shellcode content?
Common restrictions include limitations on specific characters, prohibited instructions, and restrictions on the size and complexity of shellcode.
How do these restrictions impact shellcode development?
Restrictions can hinder the functionality and effectiveness of shellcode, making it more challenging to develop and deploy malicious payloads.
Are there any exceptions or loopholes in the enforcement of these restrictions?
Certain exceptions and loopholes may exist, allowing attackers to bypass restrictions through techniques such as encoding or obfuscation.